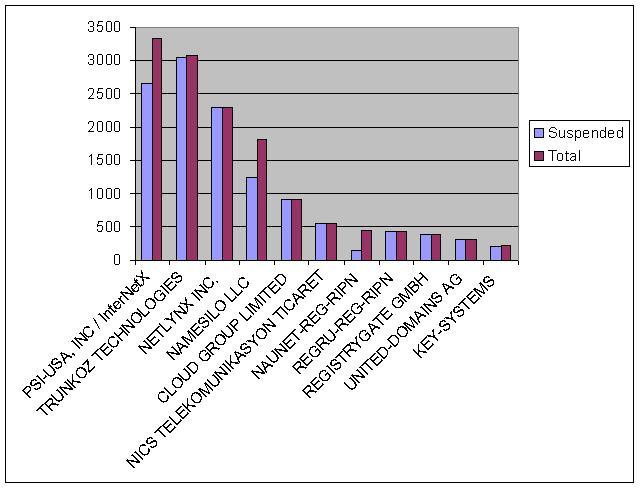
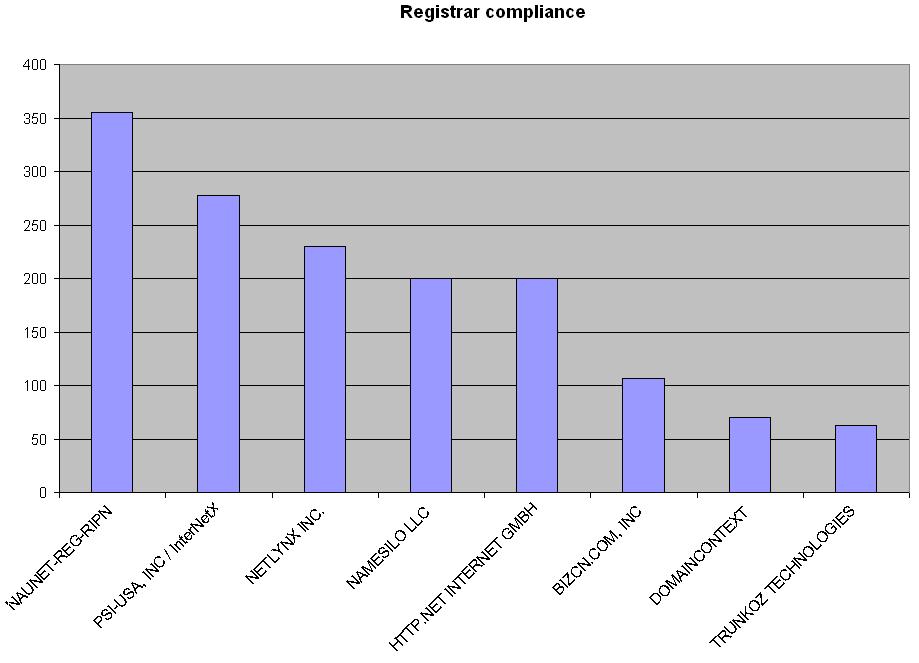
Red Dwarf wrote:
spamislame wrote:
And from there you get the typical 3-hacked-unix-server setup which has been documented previously.
I can't find evidence of that. To me it looks like they are now using just the one server for pages and images. Are you seeing something different?
Yup. A browser won't give you nearly enough info. The unix "dig" command is your friend:
Code:
%dig medicinerxtablets.ru
; <<>> DiG 9.9.3-P2 <<>> medicinerxtablets.ru
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 16817
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;medicinerxtablets.ru. IN A
;; ANSWER SECTION:
medicinerxtablets.ru. 600 IN A 91.204.162.83
;; AUTHORITY SECTION:
medicinerxtablets.ru. 600 IN NS ns1.medicinerxtablets.ru.
medicinerxtablets.ru. 600 IN NS ns2.medicinerxtablets.ru.
;; ADDITIONAL SECTION:
ns1.medicinerxtablets.ru. 600 IN A 91.204.162.83
ns2.medicinerxtablets.ru. 600 IN A 91.204.162.83
In this case all three ip addresses are the same, but in 90% of cases, they are all different.
So for example:
Code:
%dig wour.ru
; <<>> DiG 9.9.3-P2 <<>> wour.ru
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14988
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;wour.ru. IN A
;; ANSWER SECTION:
wour.ru. 600 IN A 91.204.162.83
;; AUTHORITY SECTION:
wour.ru. 600 IN NS ns1.wour.ru.
wour.ru. 600 IN NS ns2.wour.ru.
;; ADDITIONAL SECTION:
ns1.wour.ru. 600 IN A 61.178.118.4
ns2.wour.ru. 600 IN A 91.226.116.66
;; Query time: 595 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Mon Sep 23 17:38:34 EDT 2013
;; MSG SIZE rcvd: 120
So: one main http host and two dns hosts
91.204.162.83
61.178.118.4
91.226.116.66
This indicates that "91.204.162.83" is a pretty important ip for them.
Code:
%dig octh.ru
; <<>> DiG 9.9.3-P2 <<>> octh.ru
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20846
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 3
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;octh.ru. IN A
;; ANSWER SECTION:
octh.ru. 600 IN A 91.204.162.83
;; AUTHORITY SECTION:
octh.ru. 600 IN NS ns1.octh.ru.
octh.ru. 600 IN NS ns2.octh.ru.
;; ADDITIONAL SECTION:
ns1.octh.ru. 600 IN A 200.110.137.11
ns2.octh.ru. 600 IN A 125.16.213.251
;; Query time: 527 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Mon Sep 23 17:39:38 EDT 2013
;; MSG SIZE rcvd: 120
91.204.162.83
200.110.137.11
125.16.213.251
(91.204.162.83 again. Suuuuper important.)
(Note that "medicinerxtablets.ru" one is the domain from your posting way back on Feb. 20th. It's still live.)
Red Dwarf wrote:
In Firefox I use the View Page Info option, and click on Media
That will only show you the "front facing" domain, not which actual IP delivered the image content to your browser.
Red Dwarf wrote:
I would like to have a feed of Eva domains. Currrently I have to resort to all sorts of data mining tools to find them, and they are running dry.
Me too. Mine are all sporadically reported by friends who all know I'm still researching this.
I must have made some kind of impact over at Eva because they finally scrubbed their lists of all my addresses except one. It's something I honestly never expected to see take place.
SiL