|
Last visit was: Sat Jul 05, 2014 11:19 am It is currently Sat Jul 05, 2014 11:19 am |
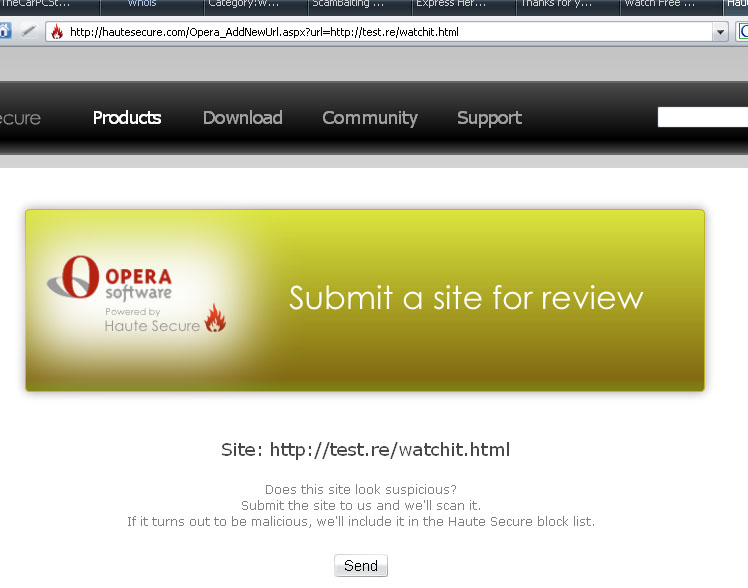
How to Report an active phishing site - [sketch] |
|
All times are UTC - 5 hours [ DST ] |
| Page 1 of 2 |
[ 19 posts ] | Go to page 1, 2 Next |
|
| Author | Message | |||
|---|---|---|---|---|
| meep |
|
|||
Joined: Thu Apr 05, 2007 4:10 pm Posts: 2777 |
|
|||
| Top |
|
| phuocngo |
|
|||
Joined: Wed Dec 24, 2008 2:27 pm Posts: 8 |
|
|||
| Top |
|
| meep |
|
|||
Joined: Thu Apr 05, 2007 4:10 pm Posts: 2777 |
|
|||
| Top |
|
| Forseti |
|
|||
Joined: Mon Jan 19, 2009 5:26 pm Posts: 6 |
|
|||
| Top |
|
| meep |
|
|||
Joined: Thu Apr 05, 2007 4:10 pm Posts: 2777 |
|
|||
| Top |
|
| phuocngo |
|
|||
Joined: Wed Dec 24, 2008 2:27 pm Posts: 8 |
|
|||
| Top |
|
| meep |
|
|||
Joined: Thu Apr 05, 2007 4:10 pm Posts: 2777 |
|
|||
| Top |
|
| Veka |
|
|||
Joined: Thu Jul 05, 2007 9:36 am Posts: 247 |
|
|||
| Top |
|
| meep |
|
|||
Joined: Thu Apr 05, 2007 4:10 pm Posts: 2777 |
|
|||
| Top |
|
| pwillener |
|
|||
Joined: Wed May 30, 2007 1:51 am Posts: 253 Location: Tokyo, Japan |
|
|||
| Top |
|
| HansTheBlueFrog |
|
|||
Joined: Wed Feb 04, 2009 3:23 pm Posts: 342 |
|
|||
| Top |
|
| Veka |
|
|||
Joined: Thu Jul 05, 2007 9:36 am Posts: 247 |
|
|||
| Top |
|
| Bobster |
|
|||
Joined: Fri Mar 23, 2007 4:16 pm Posts: 206 |
|
|||
| Top |
|
| ahoier |
|
|||
Joined: Thu Apr 03, 2008 4:33 pm Posts: 590 Location: Florida |
|
|||
| Top |
|
| AlphaCentauri |
|
|||
Joined: Thu Mar 01, 2007 3:01 am Posts: 5915 |
|
|||
| Top |
|
| Page 1 of 2 |
[ 19 posts ] | Go to page 1, 2 Next |
Inspiring websites
- Best Casino Not On Gamstop
- Nuovi Casino Online 2025
- UK Betting Sites
- Casino Not On Gamstop
- Non Gamstop Casino
- UK Casino Sites Not On Gamstop
- Best Online Casinos
- Sites Not On Gamstop
- Non Gamstop Casino UK
- Casino Not On Gamstop
- Casino En Ligne Fiable
- Non Gamstop Casinos UK
- Online Casino Nederland
- Sites Not On Gamstop
- UK Online Casinos Not On Gamstop
- Non Gamstop Casinos
- UK Online Casinos Not On Gamstop
- Casino Sites Not On Gamstop
- Meilleur Casino En Ligne Francais
- Meilleur Casino En Ligne Fiable
- Casinos Not On Gamstop
- Online Betting Sites UK
- Casino Non Aams Sicuri
- Casino Sites UK Not On Gamstop
- Migliori App Casino Online
- Casino En Ligne Crypto
- Meilleur Casino En Ligne Belgique
- Siti Scommesse Non Aams
- Casino Sans Documents
- オンラインカジノ ライブカジノ
- топ крипто казино
- ライブカジノ バカラ
- Plinko игра
- Casino Cresus
- Casino En Ligne Avis
- Siti Non Aams Sicuri
- Meilleurs Casino En Ligne
- Top Bitcoin Casinos Malaysia
- Migliori Casino Online
- Casino En Ligne Fiable
|
All times are UTC - 5 hours [ DST ] |
Who is online |
Users browsing this forum: Wayback machine and 0 guests |
| You cannot post new topics in this forum You cannot reply to topics in this forum You cannot edit your posts in this forum You cannot delete your posts in this forum You cannot post attachments in this forum |